Securing Windows, A Partially Solved Uphill Battle
Sometimes you just have (and I mean absolutely have) to run Windows. It is a rare occurrence for those with taste and discrimination, but it happens. So, what can you do to keep malicious users out of your system? Turns out there are a lot of often overlooked security hardening tips, and I plan to go through them all and how to set them up in this guide. Oh and no, antivirus software is absolutely not enough; most of the time they’re just scamming you anyway.
If you have not already tried a different operating system, just remember this before you continue. You could always switch to Linux or practically any other operating system instead of doing all of this pointless work. I say it is pointless because while this guide will make Windows a far more secure operating system than it was before, my efforts will never fix everything and nor will yours. Windows is proprietary software and as such vulnerabilities tend to be found in it faster than they are patched. This is a huge issue for businesses, and the only real fix is to invest time in learning some extra information to use Linux or put up with an army of people all across the globe trying to access your computer just because they can. If you’re interested in switching to Linux, I wrote a guide which is a good place to start.
Preparing a Virtual Machine
If you are reading this then you probably intend to secure a physical machine. For demonstration purposes, I will just be running a virtual machine on my laptop as I do not have any devices running Windows (for good reason). Regardless, everything stated here should work in exactly the same way on a physical machine or any other virtual machine.
Anyway, here’s the virtual machine we’re going to use…
Everything works, and it is an almost-fresh Windows installation. Well, let us just get right into it then.
The Basics
I am sure you have already heard these first few steps before, but let us go through them anyway. I am going to shorten it into a checklist of things you need to get started, as well as why they are required.
- A good security suite. – The mainstream ones are not going to do you any good and will likely just cost you (or if this is for a business, your company) huge amounts of money for no reason. You need a program to scan for viruses and a program to watch how software behaves. If this is for a business, you need software to make sure your users are not doing anything malicious (though you should really just get them use their own computers, as giving them a restricted experience coupled with a gateway to taking control of your entire network is a very easy way to entice someone into hacking your network). My recommendation is to stick with Microsoft Security Essentials and/or use ClamWin. For watching how software behaves, you could upgrade to ESET NOD32 coupled with Comodo Firewall.
- The ability to actually pay attention to User Account Control. It exists for a reason, you know. Do not just keep clicking “Yes” whenever a program asks for permission to do literally whatever it wants to your entire system.
- The common sense not to download anything that looks suspicious. A lot of the time you can skip over checking for viruses just by understanding that the majority of threats out there are very obvious to spot. The bigger threats actually come from software sent to you by people you know. People who have spent time with you know more about how to get around your mental defences. That is the real time you need to check a file for viruses.
Getting Rid of the Obsolete Features
Windows is old. Very old. It is also used by a lot of businesses and organisations, and they hate change because change costs time and money. So, as a result, modern versions of Windows still contain features from 1992. Shocking, right? Navigate to C:\Windows\Media and you will find some sick MIDI music designed for testing MIDI cards back then. Personally, I like onestop.mid.
Anyway, decades old music is not a security risk. You know what is though? Obsolete encryption and hashing algorithms. Obsolete systems for remotely controlling computers on a network. You know, stuff that every other operating system is capable of keeping at a reasonable standard despite also being used by businesses for plenty of years.
So, let us get started with trying to force Windows to use more up to date technologies. If there is anything we can not upgrade, we will just have to disable it outright.
The Dreaded Default SMB Shares
When you think of remote control tools that present security issues, you might think of Telnet or Teamviewer. While these may have been huge issues, the big one nowadays is a nasty little tool called “psexec”. Thankfully, Telnet is one obsolete feature that is not used anymore. Basically, psexec uses features built into the Windows service descriptively named “Server” in order to remotely execute and interact with almost any program.
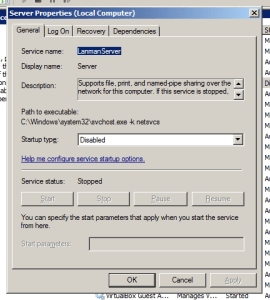
The quick way to disable it is to just to get to the “Run” dialog (With Win + R if you need reminding), type in “services.msc”, find the Server service and stop it as well as fully disable it. This is a great solution as it removes a few other possible attack vectors too, but it is only really effective on computers that are to be used for personal use.
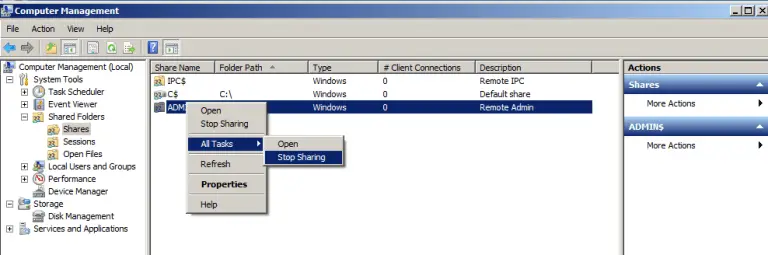
The painful way to disable it (which should only be used if you are required to use shared folders, especially on Windows Server) would be to navigate to the Computer Management panel in the Microsoft Management Console. You can do this just by typing Computer Management into the search bar in the start menu on Windows 7 through to 10. Then looking under System Tools, then under Shared Folders and then under Shares and deleting every single share with a dollar sign after its name except for the IPC$ share, as it cannot be disabled unless you disable the Server service as shown above.
Unfortunately, the problem with SMB shares does not stop there. In the section below about WPAD, you will learn about how a feature built into Windows called WPAD can reveal your password to others on the network. Unfortunately, any SMB shares you or your business have set up will do exactly the same thing. Not only that, but SMB shares can even allow remote users to execute arbitrary code on any computer on the network accessing or hosting a file share if a feature called SMB signing is disabled.
There are plenty of alternatives to using SMB shares/files shares. Part of them is just not using Windows at all. Of course, as long as you have a strong password it will make the hash of your password harder to break, thus reducing the risk. Yet still, it will always be theoretically possible to figure out your password remotely as long as an attacker has enough processing power (and I would just like to remind you that processing power is always increasing on a regular basis).
Everything else tends to use Bcrypt or Blowfish for hashing passwords (including Linux) which are two algorithms which are practically perfect for the task; the reason for this is because they are a lot more computationally intensive compared to Microsoft’s usage of MD5, MD4 and various other dated algorithms. You might think that having an extremely slow algorithm is a bad thing, but in the case of password hashing, the opposite is true. Having it take a long amount of time to compute a password hash makes it harder to guess the password as the amount of guesses you can make every second decreases significantly.
Once you have come up with a solution to getting rid of SMB once and for all, take a look at how to eliminate WPAD below (unless you actually use it, in which case… tough luck) and you will probably be a few steps closer to not having your password leaked to the rest of the network.
Dealing with WPAD
This step is huge; it is probably the most dangerous thing covered here (other than SMB). There is a tool out there called Responder that tries to convince your computer to negotiate with a remote instance of the tool rather than the services your computer is actually trying to communicate with; as such, Windows will just hand over the NetNTLMv2 hash of your password without asking any questions or even bothering to notify the user. Yes, that means that people can partly see your password just by being on the same network as you. Obviously they are only getting a hash of your password, but the algorithms Microsoft use are super weak so as technology develops you can expect these hashes to be broken extremely quickly, perhaps even by your own phone.
I would seriously recommend taking a look at all the information you can find about Responder above, as Responder does not just target SMB shares and WPAD – you’ll really want to see what it is capable of just in case you are using one of its targets on your network right now.
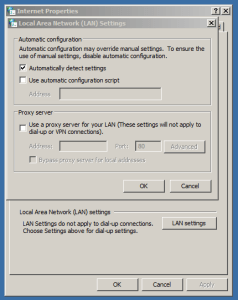
Thankfully, it is easy to prevent the damage caused by WPAD at the very least (to an extent). The best you can do is to open up the Internet Options panel, head on over to the connections tab, then click on the LAN settings button. A new window should appear, and all you need to do is uncheck “Automatically detect settings”, click OK and then you’re done.
Ultimate Windows Tweaker
There is a really cool tool called the Ultimate Windows Tweaker that you can use to change a massive amount of settings on Windows. There is only a few we will need to change in this guide, but I strongly recommend you go through all the options yourself and customise however you see fit.
So, to get started, just download the appropriate version of UWT for your version of Windows and fire it up.
Basically, you are going to want to go under the Network Tweaks tab and then tick literally every single box under Network Security, like so…

Wow, the “Enable NTLM v2 support” one really shocked me. That ought to have been enabled by default. Anyway, once you have done all that, click Apply and close UWT. Congratulations, you have made it to a point where you are mostly safe.
Some General Optimizations
So, you have managed to remove the most important obsolete features, now you want to be absolutely sure there are no cracks left. Well, of course, there still are because it is Windows. Do not worry, there are a few things left over that we can do to make you a bit safer.
First of all, keep Windows Update enabled. I am genuinely surprised by how much this is glossed over. Yes, it’s annoying. Yes, Microsoft made a terrible system for handling updates. No, it is not optional. Turn it on, make it automatic and leave it on for every single Windows computer you own. Do you have any idea how often security vulnerabilities are found in Windows? It is bad enough that the patches for them come out so slowly, it is made worse by people who turn Windows Update off.
Second, change your passwords. As shown when we disabled WPAD (which only partially fixed the problem), it is extremely easy for an attacker to gain access to the hash of your password. Luckily, NetNTLMv2 hashes cannot be used for pass-the-hash attacks (which means an attacker cannot just log into your computer remotely with just that hash), however, they still provide attackers with an infinite amount of time to crack the hash and get a hold of your real password. Surely you do not use the same password for everything, right? Well, if you do, you are going to have to start changing all of your passwords regularly and making all of them fully unique. Windows uses incredibly weak hashing algorithms (NTLM/NTHash is based on MD4… that is right it is not even MD5 and even that has security issues!) so changing your password regularly is going to be important in order to ensure that you’ve changed your password by the time an attacker has cracked it.
Third, encrypt your entire disk with something like VeraCrypt. Aside from making it impossible for people to just take your hard drive out of your computer and look at all of your files, it makes it impossible for a clever thief to steal your laptop and use the locally-stored NTLM hashes to figure out your password. NTLM is considerably weaker than NetNTLMv2 and can be used for pass-the-hash attacks, making it especially dangerous for businesses as it is very common for IT administrators to use the same password for the local administrator account on every computer, meaning an attacker could just take the NTLM hash of that account’s password from one computer and use it to take control of every single other one on the network.
Unfortunately, just encrypting your disk does not fully protect against your NTLM hashes being leaked, as you will want to find some way to prevent an attacker from having permissions to view the NTLM hashes while the system is operational. This is the hardest step, and I am not going to go into it as it is something that every IT administrator is going to have to figure out for themselves. Unlike Linux, there is always some stupid way to get administrator privileges on Windows without even providing a password. The most obscure way I have heard of was how some versions of Microsoft Office run themselves as an administrator, meaning you can insert an object into, say, a Word document that contains cmd.exe and then take over the whole system just like that. Scary, but this is also why I stated earlier that businesses would just be better off letting users use their own computers rather than invest time in worrying about whether or not someone has taken a peek at their administrator account password.
Even Deeper Security Tips
You can make a few changes in the registry as well as install a few programs that protect against things such as BadUSBs and other potential security threats. I would urge you to check out this registry rule, ConsentPromptBehaviourAdmin, which will make the User Account Control prompt actually ask for a password rather than a simple Yes/No prompt that is not exactly difficult to bypass. Additionally, I would recommend you check out this article on Duckhunter as well as buy some of these (essentially USB port blockers, except they require keys) for some decent protection against malicious peripherals. This section quite applies to Linux users too, but considering most of us use sudo anyway instead of the flawed-by-default User Account Control system on Windows, we are a little safer by default against BadUSB attacks.
How Effective Are the Above Measures?
Well, it depends. Windows is still going to be insecure as it is popular enough to have a very large amount of people working towards finding and exploiting all the problems with it. This does not bode well with the general attitude Microsoft has towards the operating system. If you have followed all the steps in this guide though, you should be okay for the most part. Do not blame me if you still get hacked though, I already told you your best bet is to just not use Windows. Even then, there are still security issues… there is just less of them. So the best you can do is just stay alert and keep track of security-related news so that you’re always ready to deal with whatever the next big threat is.
Hopefully, everything I have gone through here is good enough to protect you, but please, make sure you try an operating system like Linux if you have not already. At the very least, keep everything you care about on a computer running Linux. Just try to keep the stuff you do not want to be toasted or read by a malicious third party away from Windows as much as possible.